Smartphones on the plant floor: BYOD or company issued?
Smartphones and other devices make accessing IT/OT systems on the plant floor easier, but the use of personal devices may cause security and legal problems.

Smartphones and tablets—whether company owned or personal—must be used far away from food or beverage processing equipment to prevent potential contamination. Company-issued phones may be a safer cybersecurity bet as the IT department controls what goes on them and how they’re used. Photo courtesy of Wayne Labs
Smartphones on the plant floor: Bring your own device (BYOD) or use company-owned devices? This question no doubt conjures up a multitude of things—good and bad—for personal devices on the plant floor, for example, connecting people with equipment and company data and providing workers with actionable information on the process and maintenance to make good decisions. However, allowing the use of personal communications equipment has its own set of potential problems, such as food safety, intellectual property theft, cybersecurity, worker safety and legal issues—a potential can of worms if not handled properly.
GMPs and Phones
To begin, most food and beverage manufacturers have in place a policy that stipulates workers on the plant floor cannot have loose hanging jewelry, personal items and anything else carried above the waist that could potentially fall or be dropped into a vessel containing any substance that winds up in a food product—not to mention that a smartphone is probably one of the most unclean and difficult-to-sanitize pieces of equipment that could come into a food facility. This is simply a matter of FDA or USDA good manufacturing practices (GMPs). The same company policy typically applies in and around packaging equipment and other heavy-duty industrial machines, but mostly for safety reasons, such as keeping objects and peoples’ extremities out of dangerous equipment.

Many food companies will issue portable two-way radios that can be worn on the belt with a mic/speaker attached via a coil cord to the user’s shirt top, preventing any loss into a kettle of food. Photo courtesy of Imagemakers Inc.
In fact, FDA, in its “Good Manufacturing Practices for the 21st Century for Food Processing (2004 Study) Section 1: Current Food Good Manufacturing Practices,” outlines expectations with respect to personal hygiene and cleanliness, clothing, removal of jewelry and other unsecured objects, glove maintenance, use of hair restraints, appropriate storage of personal items, and restrictions on various activities, such as eating and smoking. The section discusses the need for appropriate food safety education and training in very general terms. A subpart further mandates the assignment of supervisory personnel to ensure compliance.1
Now the sticky issue. The National Labor Relations Act (NLRA) states in Section 7 that workers have the right to organize for the propose of collective bargaining—that in such cases have the right to take photographs, for example of potentially dangerous working conditions, though not specifically stated.2
In a case, “Cott Beverages Inc. and Joseph Kelly” (Case 16-CA-18144), an original complaint filed with the National Labor Relations Board (NLRB) took issue with the beverage company’s rules: “No personal cell phones are permitted on the manufacturing floor except for those which are company issued or approved.” The only exception is for management and leadership roles. All other electronic equipment usage is banned in manufacturing, processing and warehouse spaces.
After hearings by an Administrative Law Judge and the NLRB, the latter in May 2020 reached a decision that based on the FDA GMPs and the fact that employees could use personal phones and other equipment outside of the three areas noted, Cott Beverages was within its rights to enforce its rules. According to the NLRB findings, “nothing in the rules restrict employees from retrieving their phones from their lockers and using them on their own time when away from their workstations.”
Finally, The National Law Review (NLR) (Sept. 29, 2022) in an article entitled, “Cell Phone Use on Hold in Manufacturing Plants After Recent NLRB Decision,” noted that “unfettered employee cell phone use inside manufacturing facilities is a constant challenge for many employers.” NLR suggests that the NLRB ruling lays the groundwork for employers seeking to limit wholesale use and possession of phones during the workday.
Moreover, employers should consider three important issues in writing their policies:
- an the employer point to safety concerns it’s seeking to protect?
- Are limitations of usage focused solely on manufacturing (and other) areas where safety tantamount?
- Can employees use their phones at other locations within a plant and at other times?3
 Many food and beverage companies are within their rights to request that employees keep all electronic devices in their lockers during normal working hours.Photo courtesy of Wayne Labs
Many food and beverage companies are within their rights to request that employees keep all electronic devices in their lockers during normal working hours.Photo courtesy of Wayne Labs
Intellectual Property and Smartphones
While smartphones make many tasks easier—especially maintenance on the plant floor—whether or not they are hackable may be a secondary concern if they are privately owned and not company issued. The primary concern is they can be a repository of sensitive company data, for example, when stored away in a browser cache or in emails concerning proprietary company information such as production schedules and recipe changes. Whether it’s maintenance data or photos/videos of equipment in operation, smartphones represent an intellectual property (IP) issue if the phone falls into the wrong hands off-premises or is hacked. Phones that remain inside the plant are guarded and protected by the plant’s IT security system.
Even when intentions remain good, videos taken inside a plant may get posted to the internet, which may seem harmless enough, but could contain vital and proprietary process information, which could eventually allow a competitor to gain an advantage. Videos could be used to point out negative issues inside a company, which were not meant to be publicized. Finally, photos/videos taken and used without permission by news media could land the media company and the photographer a large lawsuit.4
Smartphones, Cybersecurity and the Plant Floor
FE invited three thought leaders to participate in a roundtable on smartphones and cybersecurity as it relates to plant floor operations. While smartphones and tablets not only use relatively secure cellular communications, most also use Wi-Fi, which can be problematic when connecting to company-based IT/OT systems. The questions for our panel members presuppose that personal devices include Wi-Fi technology.
Marty Edwards is deputy CTO – OT/IoT at Tenable, an operational technology solution protecting wired or wireless industrial networks from cyber threats, malicious insiders and human error. Prior to joining Tenable, Edwards served as the global director of education at the International Society of Automation (ISA), as well as the longest‐serving director of the U.S. Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team (ICS‐CERT).
Thomas Pace is co-founder and CEO of NetRise, which offers the ability to provide inside-out visibility and risk identification of XIoT devices. Prior to founding NetRise, Pace spent 16 years working in security across multiple roles and disciplines. From serving in the United States Marine Corps, being responsible for ICS security within the Department of Energy and most recently serving as global vice president for Cylance, Pace has been a proven leader and innovator within cybersecurity. He has also responded to hundreds of security incidents globally and shared his experience at multiple security conferences such as RSA and Black Hat.
Collin Walke leads Hall Estill’s Cybersecurity & Data Privacy practice. Prior to joining the firm, he served in the Oklahoma House of Representatives from 2016 through 2022 as the State Representative for House District 87. In addition, he was the manager for Select Legal Services, L.L.C. and provided regulatory, litigation and transactional advice to high-net-worth privately held companies and healthcare entities. Walke has over 15 years of experience in privacy matters, ranging from HIPAA to GDPR and is a Certified Information Privacy Professional-US, Certified Information Privacy Manager, and certified Artificial Intelligence systems auditor under the GDPR.
BYOD or Not…
FE: Should food and beverage processors let team members/employees use their own devices on the plant floor to interact with plant data?
Walke: “First and foremost, all manufacturing, food and beverage companies should ensure they have a personal device use policy irrespective of whether the employer allows employees to utilize their own devices,” says Hall Estill’s Walke. “With that said, use of personal devices for company business should be discouraged from a best practices perspective. Every employee who uses a personal device to access a company system increases the attack surface for bad actors. This is because individuals often use their personal devices in ways that are (or should be) prohibited by company policy. Employees are also usually far more cautious of their activities on company devices because of company oversight. Further, use of personal devices can complicate lawsuits. For example, suppose an employee has an important photograph on a personal device. Then, one day, the employee quits and takes a job out of state. That important photograph is now out of the company’s control. If the photograph was stored on a company device, it would remain with the company even after the employee leaves.”
Pace: “This should never be the case,” states NetRise’s Pace. “Phones, tablets, laptops, etc. need to be managed by the organization who possesses the data. It is impossible to know what risks or threats exist on these devices otherwise. There is a potential that an infected device could then infect the systems where the plant data is being stored or transmitted causing cascading effects for the organization as a whole. The disadvantages far outweigh the advantages which appear to only be the cost savings of the devices and management of those devices.”
Edwards: “In general, I am against allowing employees to 'Bring Your Own Device (BYOD)' within manufacturing of industrial environments,” says Tenable’s Edwards. “The risk is much too great when you are talking primarily about safety and reliability. The only perceived advantage for the company is cost, but I think the risk far outweighs that cost and only company supplied and managed devices should be used on the plant floor.”
FE: Should a food and beverage manufacturer provide its own devices rather than allow the use of BYOD equipment?
Edwards: “It is up to each company to decide if they want to use a roaming/wireless type of device on the plant floor,” explains Edwards. “If the decision is yes, then as previously mentioned, I am a proponent of only utilizing company furnished equipment for these tasks. With the proper controls and monitoring technology in place, a company can certainly limit or prevent most malware, but malware is not the only consideration here. The company has to consider other aspects of cybersecurity, such as protection of intellectual property and authentication mechanisms, as well.”
Pace: “Yes, this is the preferred approach to interact with systems that contain plant data,” Pace agrees. “Otherwise, you are simply hoping that the devices that are used are not posing a significant threat to the business. You cannot ensure that the devices are patched and up to date, free of malware or that the data leaves on those devices and then becomes available to malicious actors or even competitors. You lose all visibility and accountability of the process unless you provide the devices that need to be used. This is a significantly safer approach in terms of protecting against viruses and malware.”
Walke: “Providing company-owned devices is preferred to personal devices,” explains Walke. The advantage is several-fold: First, the device and its contents remain company property, even if the employee leaves; thereby, preserving potentially important data. Second, it decreases the likelihood of an attack because the company-owned device should have increased device controls and should only be used as permitted by company policy. Third, there is less risk of combining personal and company data. By limiting the functions of the device, and providing policies to limit unauthorized use, a company will decrease the odds of a virus or attack by providing company-owned devices.
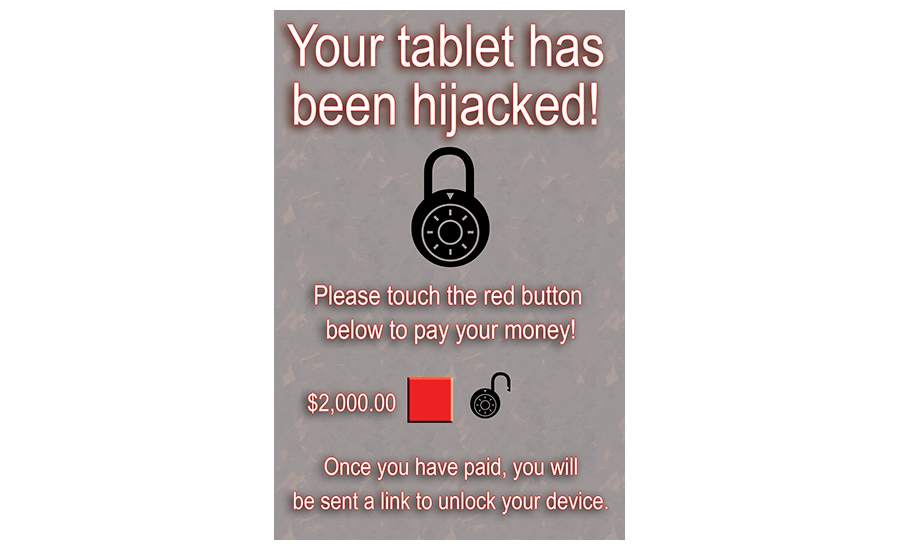 What you don’t need: An employee’s personal tablet pulls in a ransom note while connected to the company’s IT/OT network. You can only hope that this ransom note won’t find its way to other devices on your IT or OT network.Illustration: Wayne Labs
What you don’t need: An employee’s personal tablet pulls in a ransom note while connected to the company’s IT/OT network. You can only hope that this ransom note won’t find its way to other devices on your IT or OT network.Illustration: Wayne Labs
FE: If a processor specifies the use of company-owned devices to access plant data, should personal devices be allowed in the plant?
Walke: “If using company-owned devices, the company should still have a personal device use policy, and per the National Labor Relations Board, employees should be permitted access to their device during “non-work hours” (e.g., while on breaks),” states Walke. As a result, employees should be permitted to bring their devices with them to work, but a policy regarding their use outside of non-work hours should be established. There are pros and cons with regard to a policy that requires employees to lock their phones. For example, in April 2021, a shooting occurred at a FedEx facility and per FedEx’s policy, only a limited number of employees could bring their phones into the facility. Arguments have been made that if employees had access to their phones, quicker action could have been taken. Ultimately, the degree of access to personal devices while on work time is up to the employer.
Pace: “This is dependent on if any of the other systems can be accessed from arbitrary devices such as personal phones,” says Pace. “Plant systems should be built and configured in such a way that only allows trusted devices to connect to them, which should significantly mitigate the threats of these devices. Depending on the criticality of the plant and the processes being run there, it may be prudent to just not let anyone bring personal devices into the plant whatsoever, but that is dependent on a risk-based approach that each organization needs to determine on their own based on a myriad of factors. In a vacuum, yes, it is more secure for employees to not have access to their personal devices, but this may be overkill and impact employee morale in a negative manner.”
Edwards: “Being realistic, people will bring personal devices inside the plant,” warns Edwards. “Implement policies, procedures and controls to protect sensitive corporate and process data, which would include activities like taking pictures within the plant. Provide guest networks that are completely segregated from corporate and plant networks. Ultimately, plant operations must keep safety as the top priority and introducing personal devices in the plant introduces additional risk.”
 A safe place for employees to use laptops, tablets and phones is in the breakroom when they’re off hours. Many companies will provide internet services, which are free and clear of enterprise/IT/OT networks.Photo courtesy of Imagemakers Inc.
A safe place for employees to use laptops, tablets and phones is in the breakroom when they’re off hours. Many companies will provide internet services, which are free and clear of enterprise/IT/OT networks.Photo courtesy of Imagemakers Inc.
Cybersecurity and the “It Can’t Happen Here” Attitude
“Cybersecurity threats pose existential risks to companies, even though many companies simply bury their heads and hope that an attack won’t occur,” says Walke. “Unfortunately, most cyber experts agree that the question isn’t whether you will experience a cyber-attack, but rather, when? In 2021 JBS Foods paid $11 million as a result of ransomware, and Molson Coors paid $2 million for cybersecurity experts following a cyber incident that led to a system-wide outage. These threats are on top of private causes of action that often follow cyber breaches. This is why consultation with attorneys when implementing cyber risk policies and placing cyber risk insurance is so important. If a company fails to ensure that its application is correct, it could be denied coverage for a claim, and that’s assuming that the company obtained the right type of cyber coverage in the first place. The bottom line is that in the world of cybersecurity, an ounce of prevention is worth a pound of cure.” FE
References & Sources
[1] “Good Manufacturing Practices for the 21st Century for Food Processing (2004 Study) Section 1: Current Food Good Manufacturing Practices,” FDA, https://www.fda.gov/food/current-good-manufacturing-practices-cgmps-food-and-dietary-supplements/good-manufacturing-practices-21st-century-food-processing-2004-study-section-1-current-food-good
[2] “National Labor Relations Act,” Key Reference Materials, https://www.nlrb.gov/guidance/key-reference-materials/national-labor-relations-act
[3] “Cell Phone Use on Hold in Manufacturing Plants After Recent NLRB Decision,” The National Law Review, Samuel H. Ottinger & Wade M. Fricke, Sept. 29, 2022, Number 272
[4] “What’s the best way to deal with cell phones on the plant floor?” Richard Stier, FE, Oct. 17, 2016
“Smart phones on the plant floor: How secure are they?” Wayne Labs, FE, Jan. 2, 2019
 JBS was hit by ransomware in 2021and was said to have paid a $11 million ransom, according to Collin Walke. This is how the article appeared in FE on June 2, 2021. FE Magazine
JBS was hit by ransomware in 2021and was said to have paid a $11 million ransom, according to Collin Walke. This is how the article appeared in FE on June 2, 2021. FE Magazine
Cellular or Wi-Fi communications on the plant floor?
The primary concern with Wi-Fi usage is whether the connection is secure. Cellular only technology is fairly secure through encrypted connections. However, cellular technology is slower than Wi-Fi and could end up costing significant sums of money depending on the cellular plan. Further, cellular technology is limited to the device itself; therefore, reliance upon cellular technology alone may ultimately result in some devices being unusable.
—Collin Walke, Hall Estill
Wireless technology is typically going to be less secure than dedicated “hard lines.” However, cost and business efficiency are also factors in this decision. Cellular communications technology seemingly has fewer vulnerabilities than Wi-Fi, but this decision should likely be made based on access to the technology. Some areas where plants reside may have poor cellular service so Wi-Fi may make more sense. On the other side, running a dedicated internet pipe out to a plant could be cost prohibitive so cellular communication is better. If Wi-Fi is configured properly and is running on fully updated devices, it is very secure and much easier to configure than cellular technology. Wi-Fi would be my recommended solution here—all things created equal.
—Thomas Pace, NetRise
This largely depends on your infrastructure. If you have the ability to deploy cellular, and/or Wi-Fi, then our job as security professionals is to ensure the safe, secure and reliable operation for whatever technology enables the business. It isn’t a one or the other. Security is here to enable the business.
—Marty Edwards, Tenable
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






