Ransomware is big business—and you can’t afford to play the game!
A cyberattack not only creates costly downtime but also can destroy IP, cause food safety issues and just be plain expensive—whether or not you pay the ransom

Today’s “professional” ransomware hackers may operate in enemy state-controlled, well-lit and air-conditioned office buildings—and look like any other engineer behind a keyboard and screens.
Photo courtesy of Getty Images

While your machine’s HMI may not look like this when hit with ransomware, nevertheless, unprotected Windows-based HMIs and even proprietary machine controls can be stopped by a ransomware attack seemingly out of nowhere. Can you afford the downtime?
Photo courtesy Wayne Labs

Today, ransomware attacks and malware originate with state-based professional cyber-criminals as much as criminal gangs—and much less, the kid down the street.
Source: Cybersecurity & Infrastructure Security Agency (CISA) and FBI



The global damage due to ransomware attacks is expected to reach $20 billion by 2021 with a business attack occurring every 11 seconds, according to Cybercrime Magazine. Within the last week or so of writing this article, Canon worldwide fell victim to a ransomware attack. Most of Canon’s websites were down as I discovered when I couldn’t update my Digital Photo Professional camera software. Those who stored photos (not me!) on image.canon.com (Canon’s cloud) lost all their images, though Canon says the ransomware wasn’t to blame. Nevertheless, think twice before you store ANY data in the cloud without a backup “at home.”
Food and beverage not exempt
Unfortunately, most businesses—including food—don’t like to share any information about attacks they’ve sustained, hence that’s why the statistics seem like they’re all over the map. However, the industry could certainly learn by companies sharing their experiences. On June 27, 2017, Mondelēz International suffered a global cybersecurity event (Food Engineering, February 2019), which affected a significant portion of global sales and cost $84 million to resolve, says Mondelēz’s 2017 Annual Report. The company says it continues to enhance its cybersecurity efforts to minimize risks.
Mondelēz is not the only food company we know about. Sven Burkard, Belden industrial solution consultant, points to two others. (Belden is a Control System Integrators Association [CSIA] Partner Member.) First, according to a May 19, 2020 MSSP Alert!, REvil ransomware from the Sodinokibi hacking group hit Harvest Food Distributors (San Diego) and its parent company, Detroit-based Sherwood Food Distributors for $7.5 million in ransom payments. Second, according to TechCrunch.com, Arizona Beverages was knocked offline by an iEncrypt ransomware attack earlier this year, which was thought to use email to gain entry to the company’s network. Apparently, the backup system wasn’t configured correctly, and Cisco was called in to “rebuild the entire network from scratch.”
Speaking of emails leading to infection, in the course of writing this article, I received one from “Emirates NBD” (a real bank) saying my account “was simply marked in to from another Windows gadget,” advising me to click on the included “check activity” link. Another email from “Gloria Zegarra” (whomever she is and with a totally fictitious email address) suggested I download the “payment copy,” check and confirm my payment. Needless to say, our Webroot endpoint protection killed that attachment long before it could do any damage.

You probably get emails like this all the time. Thankfully, virus and endpoint protection neutralize these things so we don’t accidentally in haste click on the “attached document.”
Source: Wayne Labs
So while our virus protection software protects us from attachments, we still need to be sensitive to oddball emails potentially with very dangerous links leading to direct or downloadable ransomware attacks. For example, I’m always getting email notices from “WeTransfer.com” with curious downloadable file names that are obviously not connected to anything I’m doing. My advice? Beware! One WeTransfer email notice I just received came from a sender in Russia, that is, in the From Field, instead of WeTransfer.com, it showed pochta@uralkorona.ru. Is the .ru address real? Not likely.
Ransomware has grown up
Ransomware used to be less sophisticated than now. You clicked on something and got infected immediately—maybe through an email or fake website, infected laptop or a technician’s memory stick—and you paid the ransom within the allotted time period, got a key to decrypt your data and you were good to go until the next time. Now, the criminals have taken crime to the max—with downright extortion (as they did with Sony a few years ago and now Canon). First, often with the help of “personal engineering,” they get into your network, lurk there for days or weeks and download your sensitive files—gigabytes to terabytes of it, threaten to go public with the data if you don’t pay—and second—then encrypt your data until they get paid. And hopefully, when you pay, you get the key to decrypt your data, and it stays private.
Ransomware is on the rise because of the financial payday that is likely to follow a successful attack, says Barak Perelman, Tenable VP of OT security. Holding an environment ransom doesn’t require many resources, nor is it particularly hard to do once a security hole is found. Worse for the victim: With the advent of a traceless payment system such as Bitcoin, the chances of the hacker getting caught are few.
You’re probably familiar with software as a service or SaaS, such as Adobe’s Creative Suite or Office 365. But now there’s something new: ransomware as a service, aka RaaS. Great news for would-be criminals! They don’t have to do much—if any— programming. And like any other product, the more a hacker spends, the newer and more sophisticated the purchased product—ransomware.
“The ability for attackers to mix and match different exploits, attack payloads and compensation methods without having to do any of the coding has allowed for a large uptick in these types of attacks,” says Alan Raveling, OT cybersecurity architect, Interstates, a CSIA Partner Member. Another factor that can affect the price of RaaS purchased by attackers is the newness of an exploit. RaaS that exploits zero-day vulnerabilities (which have no fixes or patches) are rather valuable, and “service providers” (i.e., SaaS marketers—or just plain criminals) set a high price, which then slides down as more and more attackers use it, and antimalware/antivirus vendors obtain copies of it to incorporate into their defensive products.
Now, there is something new in ransomware—and much more insidious—because it can render your backups useless. Rob Pike, CEO and founder of Cyemptive, describes a situation with one client. Cyemptive has a new approach to uncovering and preventing ransomware attacks (See this month’s Engineering R&D). “We engaged with a company that handles very large amounts of data and were asked to figure out why the data and scanners were being very unpredictable, and multiple scans over the same data [were] resulting in different results,” says Pike.
“Our scanning technology found the problem in less than an hour and was able to stop the problem and prevent further expansion into their data sets. Unfortunately, ‘sleeper’ ransomware was active in this customer’s [network], and the data being accessed was working on some networks but not on others because the keys were inaccessible. What is ‘sleeper ransomware’? Sleeper ransomware is currently undetectable ransomware that slowly, stealthily infects your network over time and only when deeply embedded, activates a comprehensive attack impacting multiple levels of your operating and backup systems.”
Pike describes another client’s system where sleeper ransomware was attacking the company’s financial system while it was doing network upgrades. The business detected multiple issues on a different network and asked Cyemptive to check it out. When Cyemptive scanned the data, it found multiple active sleeper ransomware attacks in the financial system. The client was losing data daily, and Cyemptive traced the problem back five days earlier where the client’s data was encrypted, making restores impossible because of the embedded encryption. Cyemptive was able to fix the problem within two hours by scanning the backups and finding the last good backup. It could have been much worse without early detection, says Pike.
Being connected means risk, but how much?
“In their desire to be connected with their automation platforms, food and beverage processors really need to pay attention to cybersecurity,” says Steve Pflantz, CRB associate/senior automation engineer. With connectivity comes risk. Implement the proper firewalls and ensure security software is in place. The hardest part is making sure all the people that use or touch the system understand the risks and that they all practice proper cyber hygiene. Users and their actions are still the leading cause of cyber incidents.
You should take basic precautions, says Pflantz. First, don’t go crazy and have a free-for-all with new connectivity for the automation system. It is a critical part of the operation, so treat it as sacred ground and really control what is done with it. Access must be limited to only those that need it. Any unrelated equipment/software to the control system should be kept off the controls network.
While the new ransomware can lurk in backups, that doesn’t mean you shouldn’t do them. One of the key ways to defend against ransomware is to have a disaster recovery plan in place so that the system software and configuration can be completely reloaded, says Pflantz. Keep up-to-date configuration backups, and keep a copy remote or on a device that is physically separate so a ransomware attack on the control system cannot propagate to all the backups. Physical and virtual separation of a set of backups is the greatest defense against ransomware. This applies to historical data as well, so that past operating data is not lost. There will always be some risk of losing your most recent information but have a plan to do routine backups as practical.
Some basic methods to steer clear of malware and ransomware
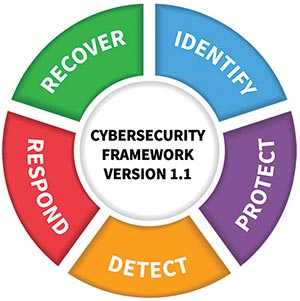
The NIST Cybersecurity Framework focuses on business drivers to guide cybersecurity activities and consider cybersecurity risks as part of an organization’s risk management process.
Source: National Institute of Standards and Technology
- Follow the basic steps in the NIST Cybersecurity Framework: identify, protect, detect, response and recover
- Remove old Ethernet-based endpoints with known vulnerabilities and no firmware updates
- Be aware of email spear phishing/phishing
- Keep potentially infected flash drives off systems
- Keep untested/personal laptops, smartphones and tablets off critical systems
- Contractors’ and integrators’ equipment should operate behind firewalls
- Software and firmware must be downloaded from only official sites—no third parties
- Unsecured networking hardware with enabled empty ports should be kept off critical systems
- Key network devices and critical equipment should be locked away out of unauthorized hands
- Deploy a zone-based security defense (ISA/IEC 62443)
- Protect and limit domain/server admin accounts
—Sven Burkard, industrial solution consultant, Belden
IT, OT…It doesn’t matter where a hacker enters your system
Brandon Ellis, president of elliTek, a CSIA Partner Member, has seen several manufacturers that have fallen prey to ransomware. These attacks were introduced on either side of the enterprise—IT and OT—and resulted in infecting the other. The severity of these attacks is varied based upon the platform. Many companies have opted to move toward PC-based, middleware systems to satisfy MES requirements and have allowed machine builders to utilize PCs alongside PLCs to meet M2M and IIoT/MES requirements. These PC-based systems automatically introduce large security vulnerabilities.
Despite IT’s best defenses, these systems are often one step behind the latest virus, malware or ransomware, says Ellis. Additional vulnerabilities can also be introduced by PC/middleware-based systems, especially if the efforts of the most vigilant IT group are disabled in order to allow key functions such as OPC communications, network connectivity, etc. for production machinery to operate correctly and within the IoT guidelines set by the manufacturer.
Ellis sees that ransomware attacks are evolving. While PC-based systems, specifically those operating within a Windows-based OS, have always been common targets, the ability to look for industrial-based systems and alter their code is occurring more frequently than in the past.
“In fact, I would estimate that nearly all PLC-based systems contain [a] single major cybersecurity oversight that could allow entire production lines to be instantly seized and held for ransom,” says Ellis. As manufacturers have added web servers—which commonly divulge the controller manufacturer, model, type and IP address all in an open HTML-based delivery—all on port 80, it’s a trivial task to discover these vulnerabilities once a malicious script comes to life and has a valid network-based host. Once underway, almost any machine can be rendered silent and force a ransom. “Of course, I am purposefully being vague,” says Ellis.
The heart of an OT environment does not run on Linux, Windows, SAP or Cisco Systems, but rather on proprietary hardware and software, says Tenable’s Perelman. These depend on the particular industrial controllers in use, typically ABB, Rockwell, Siemens, Yokogawa and the like—all of which use various industrial protocols. So while a hacker may not be able to take control of a specific industrial controller, nevertheless its files or specific areas of the network could be attacked.
Please note, however, that just because proprietary PLCs and PACs may not use a Windows OS to run doesn’t mean they’re not susceptible to direct attacks, especially if the programming system used to configure industrial controllers is Windows-based. Stuxnet was a perfect case in point. Hackers can purchase and use programming software—just like automation engineers.
Ransomware’s multiple attack vectors
Ransomware should be considered as having multiple levels of sophistication and automation, says Interstates’ Raveling. It can be configured to encrypt all devices it comes into contact with—or it can be programmed to target only specific files or encrypt only computers that have specific applications installed. More complex malware may contain additional supporting code or applications that allow it to traverse multiple operating systems, which can result in Linux, UNIX or other non-Windows operating systems to be both a target and a pivot point for additional attacks.
The most devastating ransomware attacks occur when the ransomware obtains sitewide or corporatewide administrative accounts, such as a domain administrator, adds Raveling. Limiting the usage of elevated privileged accounts and the devices on which those accounts are utilized can help to reduce the risk of these accounts being leveraged for attack. As a general practice, no user account with elevated privileges should be utilized for day-to-day or routine usage by personnel.
Automation suppliers often team with cybersecurity professionals to help users secure systems. For example, Rockwell Automation offers software and services across all five key areas of the NIST Cybersecurity Framework, which are identify, protect, detect, response and recover, says Quade Nettles, Rockwell Automation cybersecurity services product manager. Through partnerships with market-leading cybersecurity companies and Rockwell Automation OT domain expertise, the business can deploy intrusion detection and endpoint security software to protect OT assets and detect early indicators of compromise. “We are then able to leverage the information generated by these tools and offer managed services that include 24x7x365 remote monitoring of the manufacturer’s OT environment,” says Nettles.
For more details on protecting automation systems from ransomware
A continuation of this article, “Prevent ransomware attacks and save your business from financial ruin,” delves into ransomware attacks in more detail and looks at its targets and methods of protecting process control and automation systems.
October is National Cybersecurity Awareness Month. For those who like statistics, here are some scattered and alarming ones:
- Ransomware cost businesses an estimated $11.5 billion in 2019, and an average cost of a ransomware attack on a business in 2017 was $133,000, according to Sophos.
- In 2016, Datto estimated that American small businesses lose an estimated total of $75 billion a year due to ransomware. But ransomware per se isn’t the only business killer.
- Sixty percent of small companies go out of business within six months of falling victim to a data breach or cyberattack of any kind, says Layr, a commercial liability insurance provider.
For more information:
Belden, www.belden.com
CRB, www.crbusa.com
Cyemptive, www.cyemptive.com
elliTek Inc., www.ellitek.com, www.iiota.net
Interstates, www.interstates.com
Rockwell Automation, www.ra.rockwell.com
Tenable, www.tenable.com
Useful cybersecurity links:
- “How to Protect Your Networks from Ransomware,” Download, U.S. Government, Interagency, 25 AUG 2020*
- “Adulterating More Than Food: The Cyber Risk to Food Processing and Manufacturing,” University of Minnesota, Food Protection and Defense Institute, white paper, September 2019
- “NIST Cybersecurity Framework (Documents), Version 1.1,” NIST, April 2018
- “CISA Releases Securing Industrial Control Systems: A Unified Initiative,” CISA, 17 AUG 2020*
- “Industrial Control Systems: ICS CERT Advisories,” ICS-CERT, 17 AUG 2020*
- “NSA and FBI Expose Russian Previously Undisclosed Malware Drovorub in Cybersecurity Advisory,” FBI, 13 AUG 2020
- Drovorub fact sheet & FAQs, NSA, 17 AUG 2020*
- Gibson Research, search for open RDP (TCP 3389) port, GRC, 18 AUG 2020*
*Date link was recorded
Looking for a reprint of this article?
From high-res PDFs to custom plaques, order your copy today!






